OSX_GEONEI.A
OSX/Genieo.D (AVG); MacOS:Genieo-K [PUP] (Avast); Gen:Variant.Adware.MAC.OSX.Genieo.1 (BitDefender); a variant of OSX/Adware.Genieo.K (ESET-NOD32); Adware/OSX_Geonei (Fortinet); OSX/Geonei-A (Sophos); Genieo (Symantec)
Mac OS X


Threat Type: Adware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This adware arrives as a component bundled with malware/grayware packages. It may be manually installed by a user.
TECHNICAL DETAILS
Varies
Other
Yes
16 Aug 2014
Connects to URLs/IPs, Downloads files
Arrival Details
This adware arrives as a component bundled with malware/grayware packages.
It may be manually installed by a user.
Download Routine
This adware accesses the following websites to download files:
- http://{BLOCKED}-installer.{BLOCKED}t.com/install?session_id={GUID}&app_id=0&offer_id=0&os_version={OS version}&install_version=0&r={value}&disable_dynamic_update=0&active_browser=all
NOTES:
This adware does not complete its installation due to the unavailability of the accessed site.
If successfully installed, it drops the following component:
- /private/etc/launchd.conf - detected as OSX_GEONCONF.SM or OSX_GEONCONF.SMA
It accesses the following webpage once successfully installed:
It monitors websites visited by users and posts live updates of ongoing events that the users follow.
SOLUTION
9.700
10.988.07
16 Aug 2014
10.989.00
16 Aug 2014
NOTES:
- Scan using Trend Micro product and take note of the detected path.
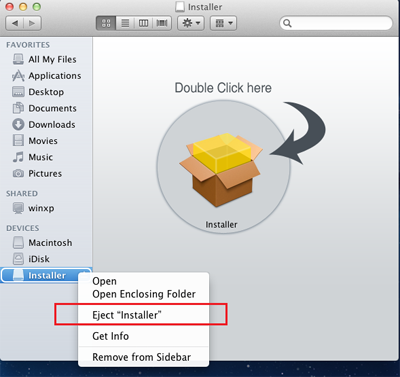
- If the detected file is mounted, EJECT the corresponding volume:
- In the Finder’s menu bar, click Go > Computer.
- In the opened window, right click on the volume where detection was seen.
- Select Eject
- Identify and terminate the running .APP process using the noted path in the previous step.
- Open the Terminal
Applications>Utilities>Terminal or type ‘Terminal’ in Spotlight. - Type the following in the terminal:
- ps –A
- Look for the detected file (commonly named as Installer.app) and take note of its PID. If the detected file is not found to be running, please proceed to the next step.
- In the same terminal, type the following:
- kill {PID}
- Open the Terminal
- Remove the detected files
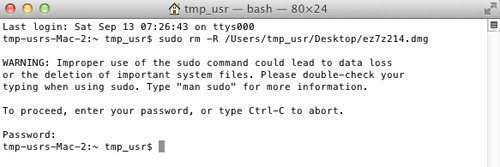
- In the same terminal, type the following and press enter:
- sudo rm –R {grayware path and filename}.dmg
- sudo rm –R {grayware path and filename}.app
- In the same terminal, type the following and press enter:
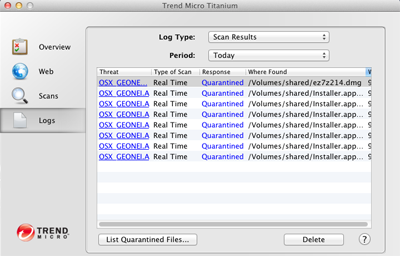
- Scan your computer with your Trend Micro product to delete files detected as OSX_GEONEI.A.
Did this description help? Tell us how we did.
